Practical Look at RISC-V Bit Manipulation and Scalar Cryptography Extensions: Benchmarking Popular Open-source Protocols and Libraries
1. Introduction
Information security is becoming increasingly important in the modern world: the number of digital devices increases every year, network technologies evolve, and the volume of processed information and internet traffic grows. Computing systems permeate all aspects of everyday life – from electricity meters and household appliances to industrial automation systems.
According to forecasts from analyst agencies, the number of active IoT connections will reach 43 billion by 2030, with a compound annual growth rate of 15%* (Figure 1). These trends are supported by statistics on registered vulnerabilities from the National Institute of Standards and Technology (NIST), considered a leading global authority on security standards (Figure 2).
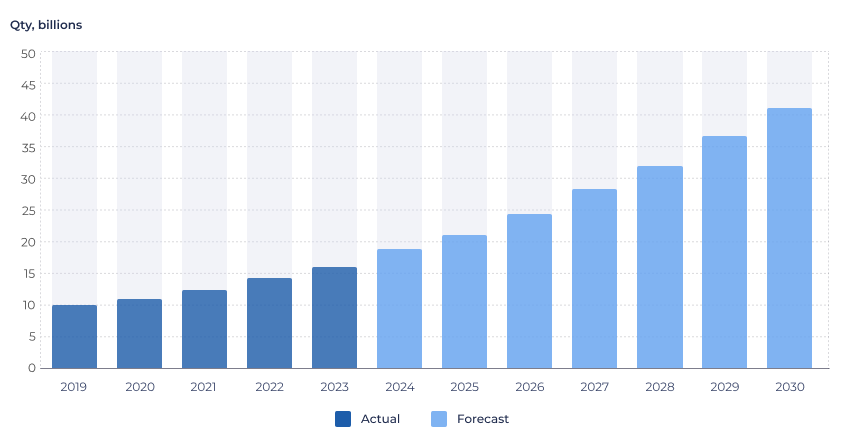
Figure 1. Total active IoT connections globally
* Data as of Q4 2024. Sources: https://iot-analytics.com/number-connected-iot-devices/
https://www.ericsson.com/en/reports-and-papers/mobility-report/dataforecasts/iot-connections-outlook
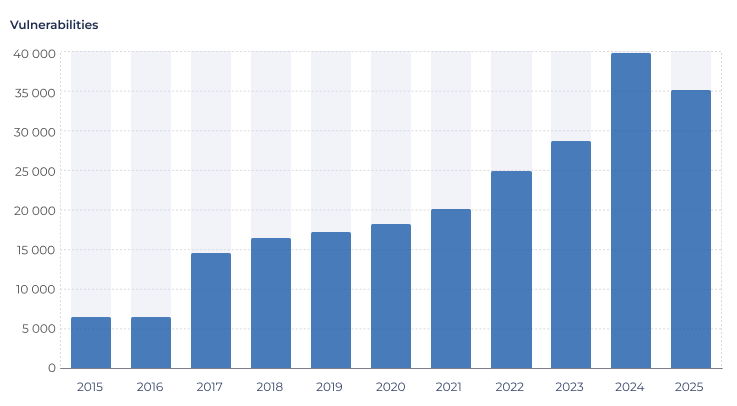
Figure 2. Cumulative count of registered cybersecurity vulnerabilities.
* Data as of 06/2025. Source: https://nvd.nist.gov/vuln/search#/nvd/home?resultType=statistics Vulnerability — a weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact to confidentiality, integrity, or availability. https ://nvd.nist.gov/vuln
Current trends in information security have led to the emergence of national legislative requirements, such as the GDPR in Europe, CCPA in the US, and CSL in China, which require responsibility for the protection of personal data, including email addresses, IP addresses, and other personal information. Furthermore, various countries have developed and are advancing national cryptographic standards aimed at ensuring the technological sovereignty and independence of states in the area of information security.
Creating a fully secure computing device requires the implementation of a set of measures, including, for example, memory protection, secure boot, control flow integrity (CFI), and much more. This article focuses on one of the aspects of building a robust system — security at the ISA level — specifically examining the RISC-V Bit Manipulation and Scalar Cryptography extensions, which play an important role in ensuring strong cryptographic security. We will review modern encryption algorithms, including national ones, examine the specifics of their implementation based on the ISA, and conduct comparative performance tests of RISC-V MCU and APU IP cores developed by Syntacore.
2. Modern Cryptographic Algorithms Overview
Modern security challenges have motivated the community to enhance existing security approaches. In particular, this has led to the development of open-standard algorithms, where the key's secrecy, rather than the algorithm's secrecy, is important. Furthermore, increasing key lengths has become a crucial factor, as increasing computing power increases the risk of hacking, requiring algorithms to ensure a higher level of security.
Let's examine the key features of the most well-known and widely used encryption algorithms and hash functions.
AES (Advanced Encryption Standard)
AES, a symmetric block cipher based on the Rijndael algorithm, replaced the outdated DES (Data Encryption Standard) in 2001 and supports keys up to 256 bits long. AES has become the global symmetric encryption standard adopted by NIST, withstanding decades of research and practical use, and is still in use today. It is effectively implemented in both software and hardware. It is widely used in applications such as HTTPS (TLS), disk encryption, and IoT data protection.
SHA (Secure Hash Algorithm)
The most widely used hash functions are SHA-2 and the more modern SHA-3. SHA-2 includes several variants with hash lengths of 224, 256, 384, and 512 bits, providing a higher level of security. These functions are widely used for data integrity verification, digital signatures, authentication, and password storage, providing protection against alteration and tampering.
SM3/SM4 (ShangMi 3 and ShangMi 4)
National Chinese algorithms SM3 and SM4. SM3 is a 256-bit cryptographic hash function, similar to SHA-256. It is used to generate digital signatures, verify data integrity, generate keys, and facilitate authentication processes. It competes with international standards and is widely used to secure wireless networks and transactions. SM4 (ShangMi 4) is a symmetric block cipher (128-bit block size, 128-bit key). It has been adopted as both a Chinese national standard and an international data encryption standard. It is widely used in China to secure wireless networks (WAPI), financial transactions, government platforms, and VPNs.
3. ISA-based Encryption Implementation
As already noted, the increasing volume of global traffic and the rising number of computing devices continuously demand higher performance. Software-based encryption often heavily loads the CPU, creating a bottleneck that restricts processing speed, throughput, and system responsiveness. What is more, the proliferation of compact, battery-powered devices requires greater energy efficiency, which is difficult to achieve with CPUs that execute thousands of instructions for encryption, decryption and signature calculations.
Another important issue is vulnerability to side-channel attacks, where the execution of algorithms can be monitored and analyzed, enabling attackers to identify specific patterns and recover secret keys. This issue is particularly significant for resource-constrained devices like IoT devices, where implementing robust security measures is challenging, making them especially vulnerable to such attacks.
Finally, standardization is an important aspect. As SoCs are complex devices, compatibility across solutions from different manufacturers helps unify requirements for architecture, protocols, security algorithms, and testing methods, thereby simplifying component integration and boosting overall system reliability.
In the context of processor architecture development, the concept of creating processors that implement cryptographic functions at the instruction set (ISA) level, capable of meeting both national standards and international requirements has become relevant.
Many modern architectures, such as x86 and ARM, incorporate extensions to accelerate cryptographic algorithms and enhance security. RISC-V is no exception — its modular design provides new opportunities for improved security through specialized extensions — Bit Manipulation (officially "B") and Scalar Cryptography ("K"). Let’s explore these in more detail.
Bit Manipulation
A dedicated bit manipulation extension designed to accelerate operations with bits such as shifts, masking, and logical operations that are common in various algorithms: cryptography, data compression, coding, and others. While not specifically part of cryptography, it is widely utilized within cryptographic processes.
Main sub-extensions:
- Zba (Address generation) — instructions for accelerating address calculations
- Zbb (Basic bit-manipulation) — bit operations
- Zbc (Carry-less multiplication) — instructions for multiplication without carry
- Zbs (Single-bit operations) — instructions for working with individual bits
Scalar Cryptography
An extension designed to accelerate standard cryptographic algorithms and primitives. Unlike other architectures, the RISC-V Scalar Crypto extension utilizes GPR registers and handles small operands (32 and 64 bits), making it a flexible and cost-effective solution, particularly for embedded cores where minimal area and high performance are essential.
Main sub-extensions:
- Zkne/Zknd — commands for AES encryption and decryption
- Zknh — commands for the SHA-2 family of hash functions
- Zkse/Zksh — commands for the Chinese SM4 block cipher and the SM3 hash function
- Zkr — provides access to a hardware entropy source
- Zkt (Data-independent execution latency) — ensures that the execution of a specific instruction set is data-independent
- Zbk (Zbkb, Zbkx, Zbkc) — selected subsets of commands from the "B" extension, critical for cryptography, including bitwise operations such as byte reversal and carry-less GCM multiplication etc
4. Hands-on Performance Evaluation Results
Syntacore's microcontroller and application-class cores support Bit Manipulation and Scalar Cryptography extensions, fully compliant with RISC-V architecture specifications. This allows the development of SoCs that can efficiently handle encryption, data integrity verification, and hashing tasks with widely-used algorithms.
This section demonstrates how the Bit Manipulation and Scalar Cryptography extensions enhance the performance of AES and SM4 encryption algorithms in practical applications across MCU and APU-class cores. It focuses on data transfer and disk encryption scenarios utilizing SCR4, SCR5, and SCR9 cores. The performance results for other MCU (SCR3 and SCR6) and APU (SCR7) cores in Syntacore’s portfolio are comparable to those shown below.
Algorithm Encryption Performance for MCU Cores
SM4-ECB for fixed-size packets
- Platform: SCR4 32-bit
- Algorithm: SM4 (ECB)
- Source: RISC-V Crypto Benchmarking
An implementation of SM4 in the ECB mode (where each data block is encrypted independently) with fixed-length packets. The input data is the data block size — N (1360 bytes) and the total payload processing time in cycles (Payload). The performance indicator (Payload/N) — the inverse of the throughput indicator — is the number of cycles required to process a single byte of data.
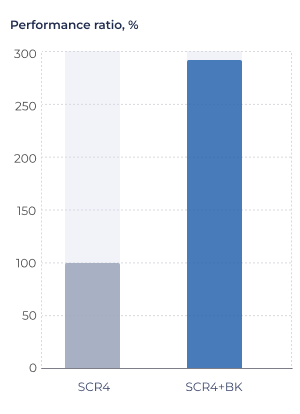
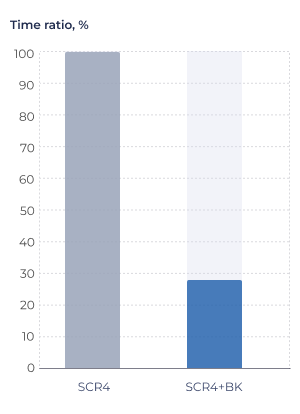
Figure 3. SM4 algorithm performance evaluation.
Conditions: SC-DT 2025.09, LLVM-20-sc, O3
Algorithm Encryption Performance for APU Cores
AES-128-CTR in NB-IoT
- Platform: SCR5, Linux 6.12
- Algorithm: AES-128-CTR
- Library: OpenSSL
- Network stack: NB-IoT
A traffic encryption scenario involving the processing of packets of varying sizes ranging from 16 to 16,384 bytes.
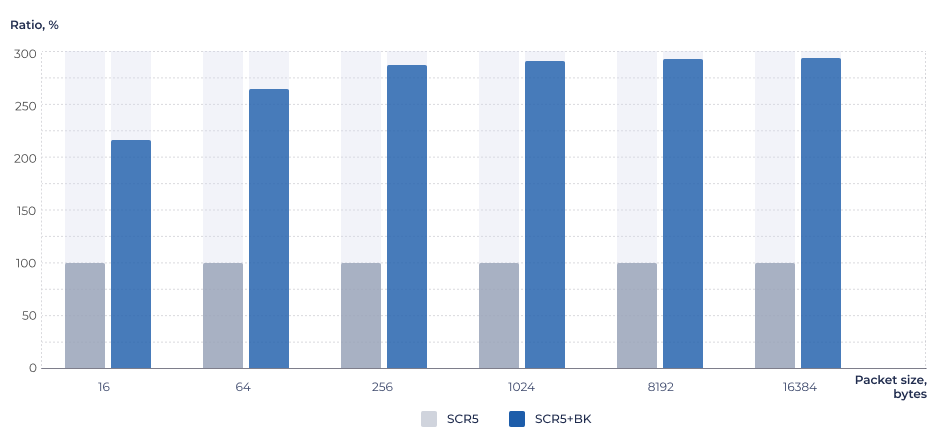
Figure 4. AES-CTR algorithm performance comparison.
Conditions: SC-DT 2025.06, LLVM-19-sc
Network traffic encryption with AES-GCM
- Platform: SCR9, Linux 6.6
- Algorithm: AES-GCM
- Library: OpenSSL 3.4
A scenario of downloading a file from a network using wget over a secure channel. AES-GCM (Galois/Counter Mode) is an encryption mode that combines symmetric AES encryption with data authentication, ensuring both message confidentiality and integrity.
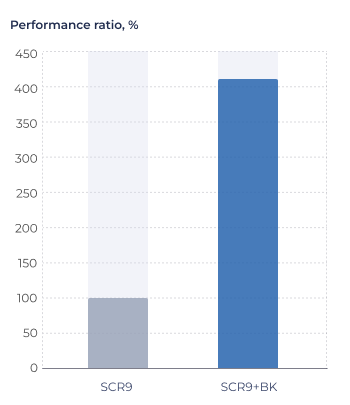
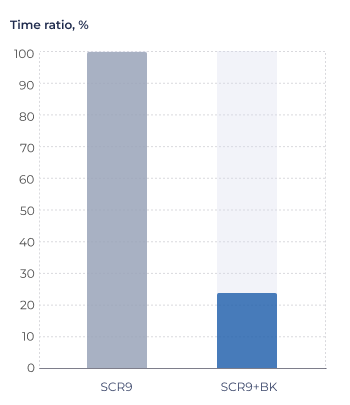
Figure 5. AES-GCM encryption performance evaluation.
Conditions: SC-DT 2025.03, LLVM-19-sc
Measurements with wget include significant network stack overhead, which distorts the actual encryption performance speedup. To obtain a more accurate assessment of the cryptography-related part of the workload, these measurements are supplemented with data from a standalone AES-GCM cipher processing 1480-byte packets (Figure 6).
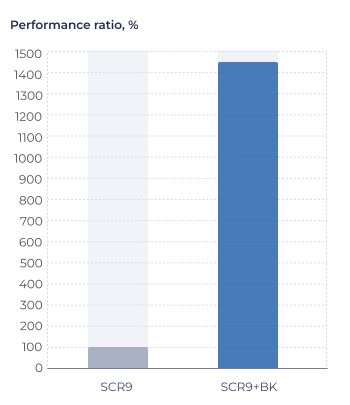
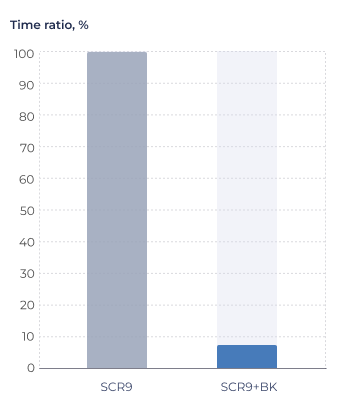
Figure 6. Standalone AES-GCM encryption performance evaluation.
Conditions: SC-DT 2025.03, LLVM-19-sc
Disk encryption using AES-128-XTS
- Platform: SCR9, Linux 6.12
- Algorithm: AES-128-XTS
- Library: OpenSSL 3.4
A disk encryption scenario comparing two data block sizes: the standard 512-byte block and an extended 4096-byte block optimized for NVMe devices. The test runs for 5 seconds using the AES-128 algorithm in XTS mode, which is specifically designed to safeguard data on disks and file systems.
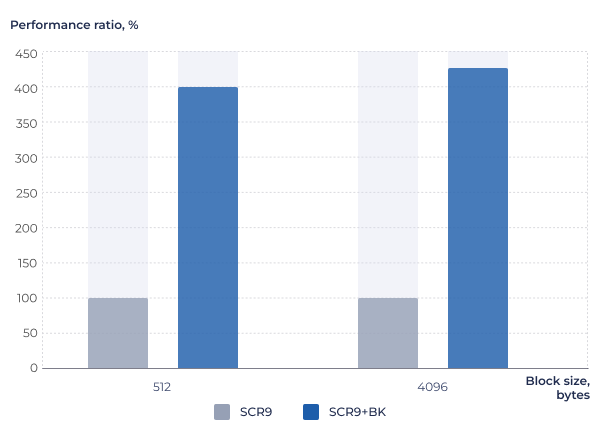
Figure 7. AES-XTS performance evaluation in a disk encryption scenario.
Conditions: SC-DT 2025.09, LLVM-20-sc
Practical tests demonstrate a significant increase in encryption performance across all tested algorithms compared to the generic implementation:
- SM4, AES-CTR — up to x3
- AES-GCM, AES-XTS — up to x4
- AES-GCM (standalone) — up to x14
The results confirm the advantages of utilizing specialized cryptographic extensions in the observed scenarios.
5. Summary
In today's world, security is becoming increasingly important, as the number of threats increases each year, and their complexity and diversity grow. Information security issues are addressed at the national level by implementing security standards and regulations to strengthen protection and prevent potential risks.
The issue of device security is complex and requires consideration of multiple factors. In this article, we focused on one such factor — implementing encryption at the instruction set level of the RISC-V architecture (Bit Manipulation and Scalar Cryptography extensions), highlighting its advantages over general-purpose software solutions. Practical tests using Syntacore SCR4, SCR5, and SCR9 cores, along with AES and SM4 algorithms in various modes and scenarios, demonstrated that the use of specialized extensions provides a significant performance boost. This makes the implementation of such a mechanism both feasible and fully justified when designing computing devices that meet modern international security requirements.